Cloud Based Security Services

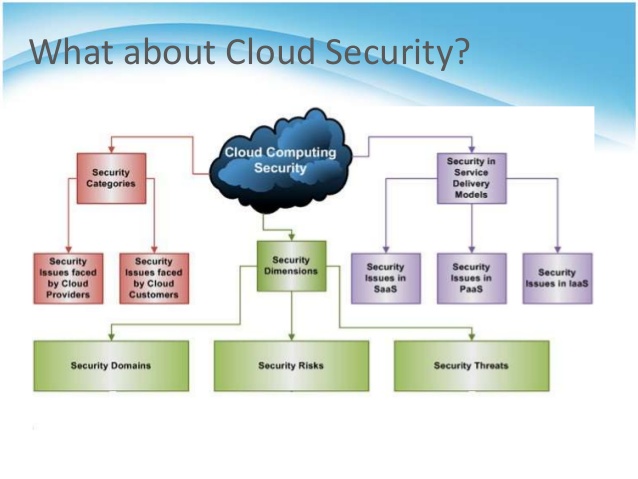
The responsibility of securing cloud lies on the customer and the service provider.
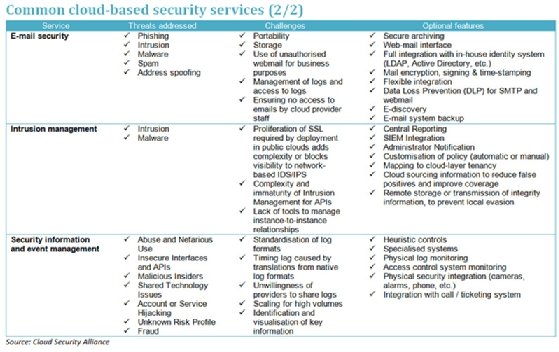
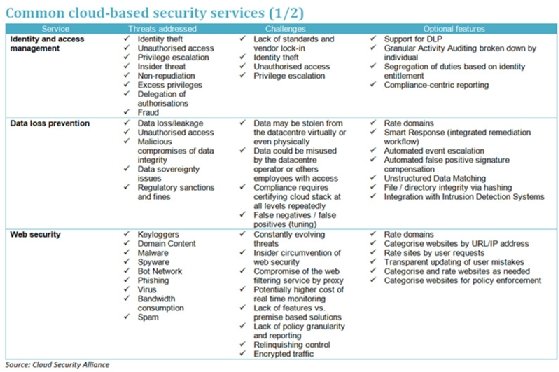
Cloud based security services. Despite these perks there is simply no shying away from cloud s inherent security issues. Large clouds predominant today often have functions distributed over multiple locations from central servers. Network security services located in the cloud provide agencies and other government entities with customized access protection for their private networks. Here are the top 10 security threats to cloud based services businesses must be prepared for.
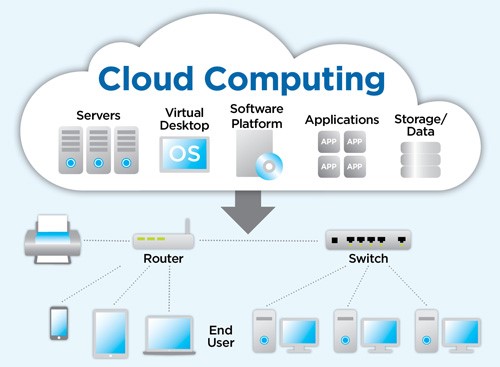
According to cloud security alliance csa over 70 percent of the world s businesses now operate at least in part on the cloud. With benefits like lower fixed costs higher flexibility automatic software updates increased collaboration and the freedom to work from anywhere 70 percent isn t a big surprise. Cloud computing is the on demand availability of computer system resources especially data storage cloud storage and computing power without direct active management by the user the term is generally used to describe data centers available to many users over the internet. It s a centralized approach to security capable of protecting sensitive data supporting compliance efforts and setting authentication rules.
Cloud based security providers have come up with cloud based security solutions to ensure that a customer s information and data are secure. Cloud or cloud computing security refers to the set of procedures technologies policies and controls that come together to protect information on cloud based servers. Although it s becoming safer by the year a number of threats still linger that businesses should prepare for. The most important aspect of cloud based security is to ensure that only authorized personnel access the cloud.
Read google drive review. Gartner is predicting the cloud based security services market which includes secure email or web gateways identity and access management iam remote vulnerability assessment security. Firewall vpn intrusion prevention services and secured remote access vpn are bundled together to create a complete security solution. Cloud security also known as cloud computing security consists of a set of policies controls procedures and technologies that work together to protect cloud based systems data and infrastructure.