Cloud Security And Privacy

A security and privacy framework for rfid in cloud computing was proposed for rfid technology integrated to the cloud computing which will combine the cloud computing with the internet of things.
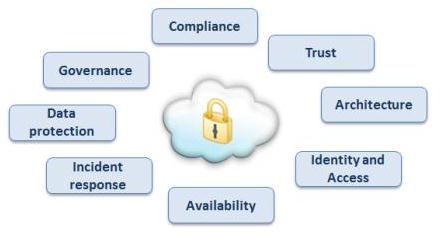
Cloud security and privacy. Explore the path to universal policy management in this webinar. Get up to speed on cloud security and privacy and selecting the right encryption and key management in techbeacon s guide. Navigating the dimensions of cloud security and following best practices in a changing business climate is a tough job and the stakes are high. Discover ways to take advantage of the flexibility o.
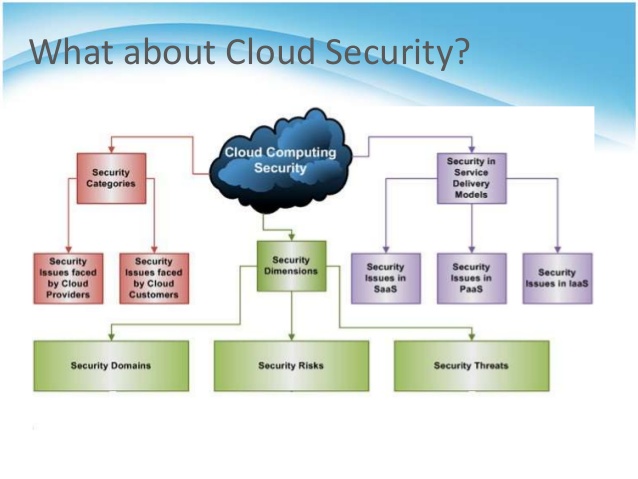
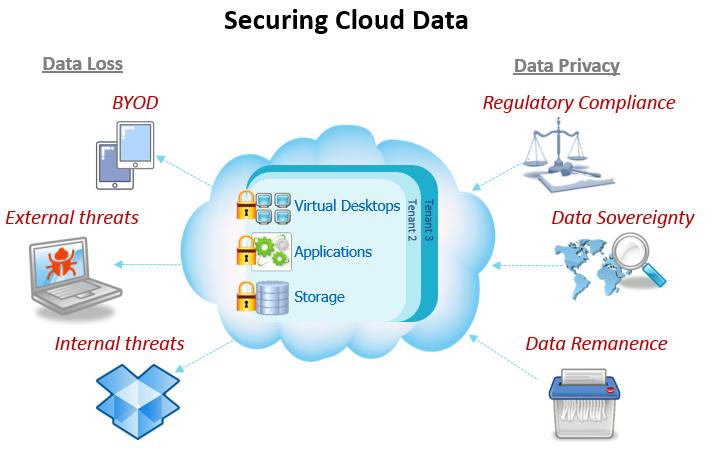
These cloud computing security measures are configured to protect data support regulatory compliance and protect customers privacy as well as setting authentication rules for individual users and devices. Recent advances have given rise to the popularity and success of cloud computing. As birk 2011 pointed out most discussion so far is centred mostly around cloud security data privacy and data protection. You ll learn detailed information on cloud computing security that until now has been sorely lacking.
Security as a service provided by cloud based platforms is recognized as the best solution to this challenge pravin kothari. Help keep your organization secure and compliant with google cloud. But to date. Cloud security consists of a set of policies controls procedures and technologies that work together to protect cloud based systems data and infrastructure.
Ideal for it staffers information security and privacy practitioners business managers service providers and investors alike this book offers you sound advice from three well known authorities in the tech security world. The article concludes with a discussion on future research directions that might lead to more trustworthy cloud security and privacy. However when outsourcing the data and business application to a third party causes the security and privacy. While there has been a great deal of attention paid to the promise of cloud computing there has also been considerable skepticism about the security and privacy of cloud computing.
Generating business insights based on data is more important than ever and so is data security.